Today's organizations are trying to cope up with exponential growth of personal mobile devices that try to access the enterprise network. The mobile devices present unique problem to network administrators since they are putting the corporate networks at risk. The network administrators need the tools to control the network access, get more visibility into the network and comply with the organization policies while strengthening their network security.
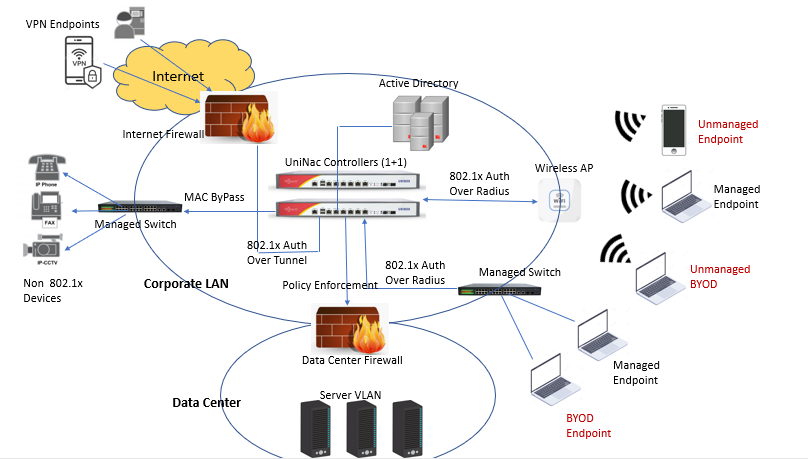
Network Access Controllers are responsible hardening the security of the enterprise network by controlling access of endpoints to the network resources and by enforcing security policies on each device. The overall objective of NAC is to make better decision about which device get network access and what the device is allowed to do on the network. The NAC is also responsible for limiting or restricting endpoints to network resources based on the policies defined for the organization.
All-in-one Access Controller
for Enterprise Networks
Integrates Access Control, RADIUS service, 802.1x and MAC authentication, LDAP/AD integration, VPN server, AP Controller, Policy Management, Firewall and many functions in a single appliance
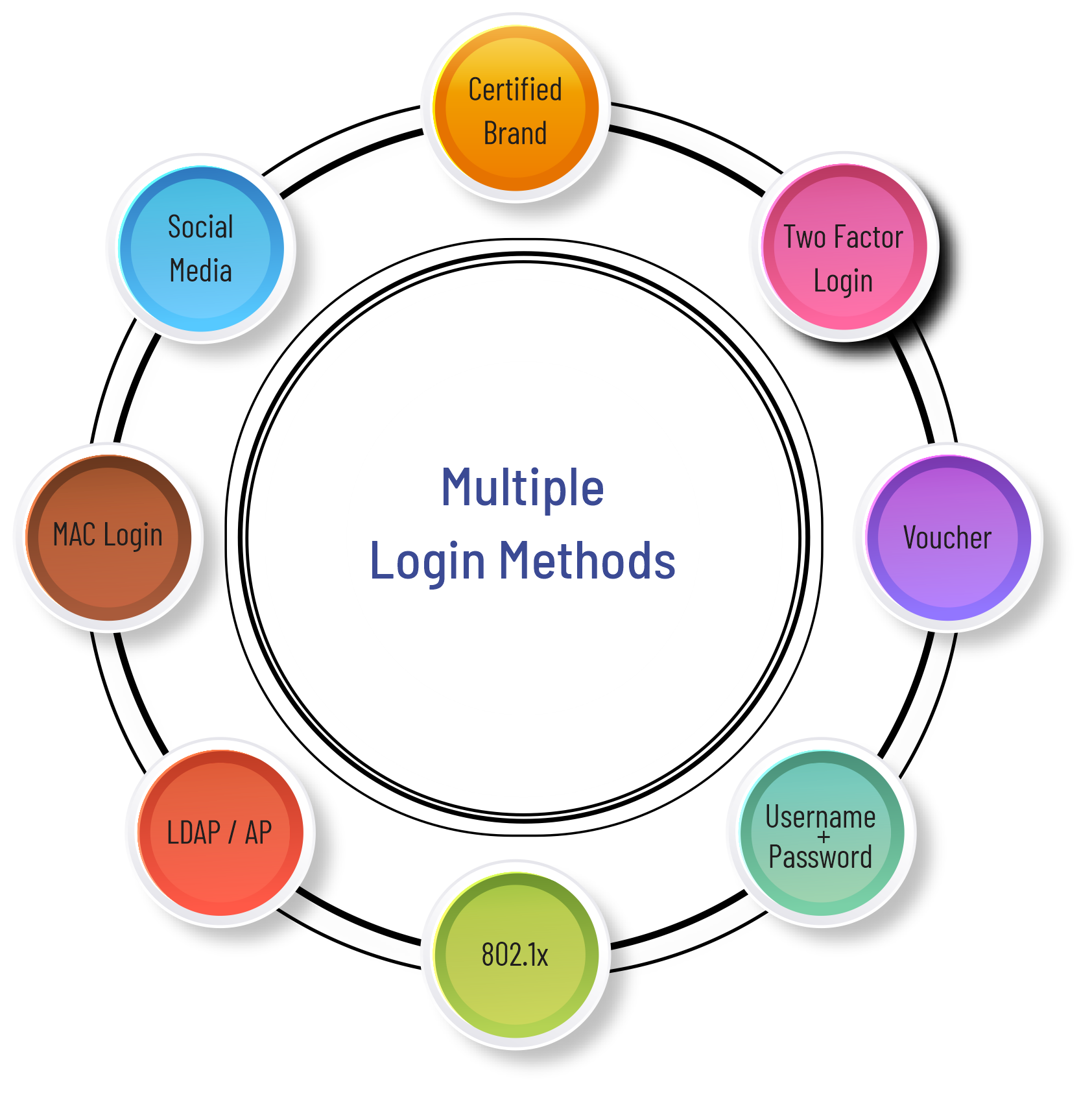
Over 12 different login methods
with built-in Portal server
Click-through Login, Social Media (Facebook, Twitter, LinkedIn), SMS/OTP, Prepaid Vouchers, Paid Portals, LDAP/AD, 802.1x, MAC-based and other login methods.
Mobile Device Management
Manage and track all the mobile devices on the network. Enable automatic mobile device registration using approval based method. Complete visibility into user behaviour and activity on the network.
Want to learn how Network Access Controllers can benefit your business?
Call Us Now For Online Demo
Powerful Analytics
NAC provides powerful analytics and reporting to monitor all the network activity. Provides insights into user activity, traffic flow and malicious activities on the network. Network diagnostics gives visibility into network issues, application usage and port traffic.
Keep Network secure
Build security layers to ensure your networks are safe from hackers, external / internal attacks, malicious users, rogue access points and unauthorized users. Offers multiple security feature like 802.1x authentication, guest access, VLAN isolation, VPN service, Content Filtering, enterprise-level firewall and lot more